Identity and Access Management (IAM)
This page explains how to control access to devices using Identity and Access Management (IAM). Access privileges can be assigned at the subscription level and cannot be managed at the individual device or registry level. Typically, access is granted to individuals or groups of users. For information on device security, which uses public/private key authentication, please refer to the section on device security.
For instance, if you assign a user the role of a provisioner in an IAM policy for a subscription, that user will have the ability to add or remove devices, but will not be able to modify or delete the registry itself.
Managing Users
You can manage the users in your current OmniCore subscription by navigating to the IAM > Users section. Users can be added using their email address, which must belong to the tenant domain. For example, if your organization domain is @example.com, only users with the same domain can be added. There is an exception for adding Partner staff, which will be described in the Partner section below.
Roles
A role is a collection of permissions. For example, the role of "roles/viewer" includes the permissions "registries.get," "registries.list," "devices.get," and "devices.list." Roles are assigned to users to grant them the ability to perform actions on the registries within your subscription.
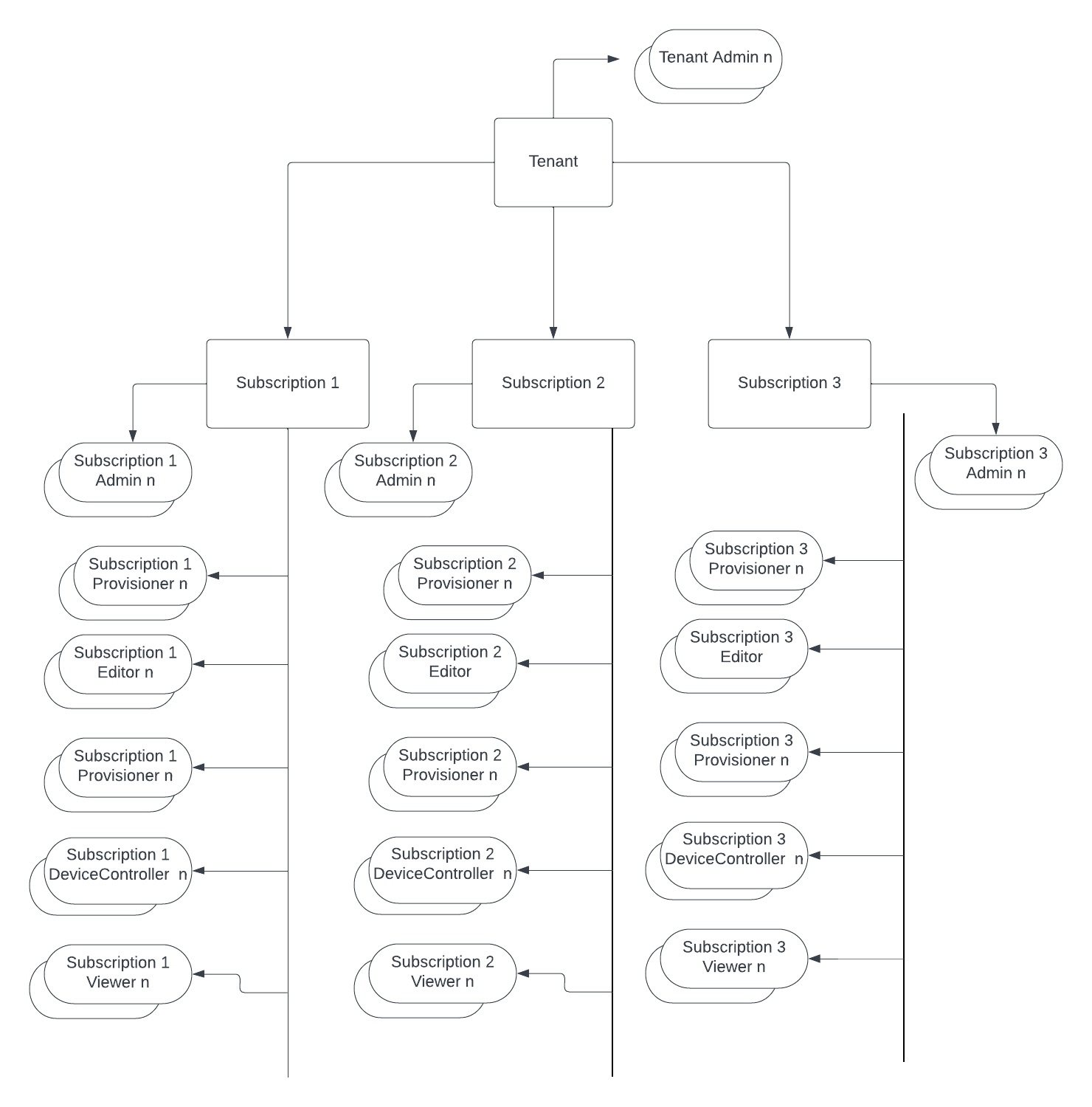
The following table lists the OmniCore IAM roles, including the permissions associated with each role:
| Role | Description | Permissions |
|---|---|---|
| Viewer | Read-only access to all OmniCore resources | omnicore.registries.get omnicore.registries.list omnicore.devices.get omnicore.devices.list omnicore.sinks.list omnicore.apikeys.list omnicore.metrics.get omnicore.subscription.get |
| DeviceController | Access to update the configuration of devices, but not to create or delete devices | All of the above and: omnicore.devices.updateConfig omnicore.devices.sendCommand |
| Provisioner | Access to create and delete devices from registries, but not to modify the registries | All of the above, and: omnicore.devices.create omnicore.devices.delete omnicore.devices.update omnicore.devices.bindGateway omnicore.devices.unbindGateway |
| Editor | Read-write access to all Cloud IoT resources | All of the above, and: omnicore.registries.create omnicore.registries.delete omnicore.registries.update omnicore.audits.list |
| Admin | Read-write access to all User and Identity Provider resources | All of the above and: omnicore.users.list omnicore.users.create omnicore.users.delete omnicore.users.update omnicore.users.get omnicore.roles.list omnicore.roles.get omnicore.providers.list omnicore.sinks.create omnicore.sinks.delete omnicore.sinks.get omnicore.apikeys.create omnicore.apikeys.delete omnicore.apikeys.getKey omnicore.partners.list omnicore.partners.create omnicore.partners.delete omnicore.migration.listBatches omnicore.migration.getKey omnicore.migration.createKey omnicore.migration.startMigration omnicore.migration.getBatch omnicore.migration.resolveConflict omnicore.subscription.audits |
| TenantAdmin | Full control of Tenant. Access to all subscriptions under the tenant | All of the above and: omnicore.tenant.update omnicore.tenant.audits omnicore.users.resetPassword omnicore.users.disableUser omnicore.users.createTenantAdmin omnicore.users.updateTenantAdmin omnicore.users.deleteTenantAdmin omnicore.providers.create omnicore.providers.delete omnicore.providers.update omnicore.providers.get |
| APIReader | Read-only access to Devices and Registries | omnicore.registries.get omnicore.registries.list omnicore.devices.get omnicore.devices.list |
| APIController | Access to update the configuration of devices, but not to create or delete devices | omnicore.registries.get omnicore.registries.list omnicore.devices.get omnicore.devices.list omnicore.devices.updateConfig omnicore.devices.sendCommand |
| APIAdmin | Backend Application invoking OmniCore through API | omnicore.registries.get omnicore.registries.list omnicore.devices.get omnicore.devices.list omnicore.devices.updateConfig omnicore.devices.sendCommand omnicore.devices.create omnicore.devices.delete omnicore.devices.update omnicore.devices.bindGateway omnicore.devices.unbindGateway omnicore.registries.create omnicore.registries.delete omnicore.registries.update omnicore.sinks.list omnicore.sinks.get omnicore.sinks.create omnicore.sinks.delete omnicore.metrics.get |
Identity Management
OmniCore uses GCP Identity Platform for User Management. The default Identity provider in OmniCore is Email/Password. But you can enable SSO with your organization Identify platform by using the SAML sign in Provider. To configure the SAML provider
- Go to the console.
- Choose IAM and under provider click the Add a Provider button.
- From the dropdown, select the SAML option.
- Enter the following details:
- The Name of the provider. This can be the same as the provider ID, or a custom name. If you enter a custom name, click Edit next to Provider ID to specify the ID (which must begin with saml.).
- The provider's Entity ID.
- The provider's SAML SSO URL.
- The certificate used for token-signing on the provider. Make sure to include the start and end strings. For example: Certificate start and end strings
-----BEGIN CERTIFICATE-----
MIICajCCAdOgAwIBAgIBADANBgkqhkiG9w0BAQ0FADBSMQswCQYDVQQGEwJ1czEL
...
LEzc1JwEGQQVDYQCwsQMSBDAF0QAB0w9GikhqkgBNADABIgABIwAgOdACCjaCIIM
-----END CERTIFICATE-----
- Under Service provider, enter the Entity ID of your app. This is typically your app's URL. On your SAML identity provider, this is referred to as the audience.
- Add your app to the list of Authorized Domains. For example, if your app's sign-in URL is https://example.com/login, add example.com.
- Click Save.
Partner
f you have an OmniCore Partner serving as your System Integrator, you can grant access to your OmniCore subscription for their staff. To do this, you first need to add the Partner to your subscription, which can be done in the IAM section. Simply click on the "Add Partner" option, and enter the partner code provided by your partner. After adding the Partner, you can grant access to their employees for the current OmniCore Subscription.
The partner association to your subscription will depend on the chosen Deployment Option.