Zero Touch Provisioning
Zero Touch Provisioning (ZTP) eliminates the need for manual device provisioning through the API or Console. With ZTP, devices can self-provision on their initial connection to OmniCore. In order to enable self-provisioning, the device must send a Bootstrap certificate in the username field of its MQTT Connect request. The Bootstrap certificate needs to be added only to the Username field in the provisioning request. Once the device is provisioned, it can simply send the word 'unused' in the Username field for all future MQTT Connect requests.
Instructions for Generating a Signed Bootstrap Certificate:
- To start, generate a device key pair consisting of a private key and a public key.
- Next, create a CSR and submit it to a trusted CA (such as an internal CA or a recognized external CA).
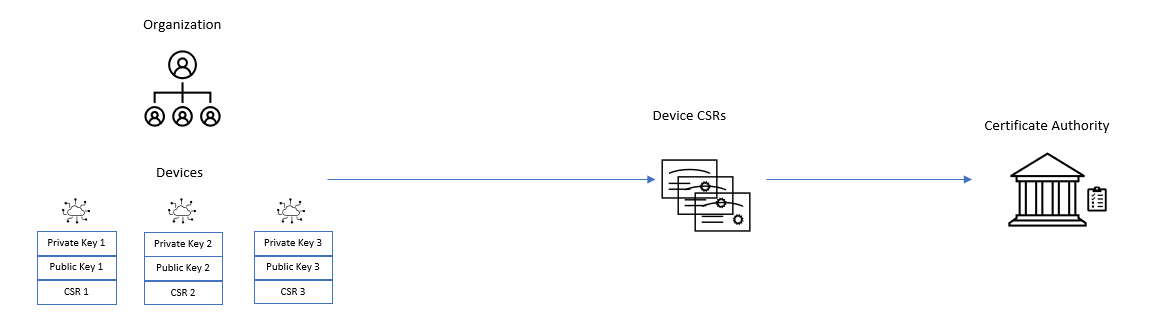 3. Once the certificate is signed, it becomes a potential Bootstrap certificate in OmniCore.
3. Once the certificate is signed, it becomes a potential Bootstrap certificate in OmniCore.
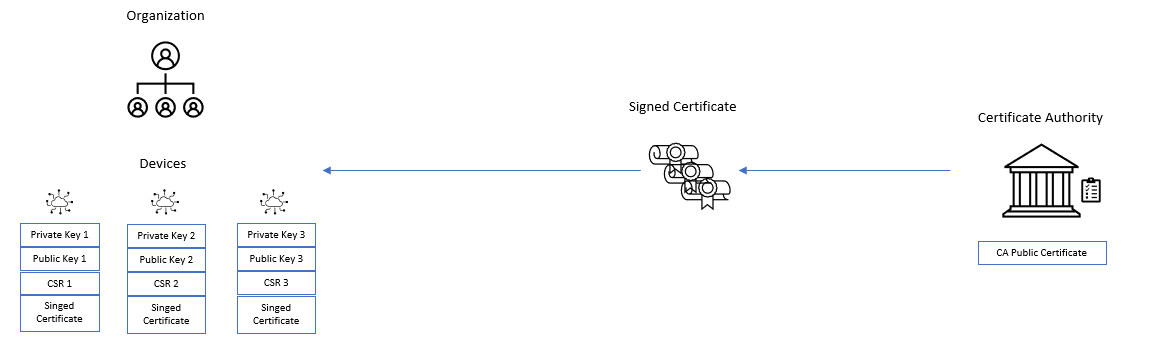
- The CA public certificate should then be added to the Registry CA certificate list using either the console or API.
- Finally, include the Bootstrap certificate in the MQTT Username field when connecting the device to the registry for the first time.The Bootstrap certificate needs to be added only to the Username field in the provisioning request. Once the device is provisioned, it can simply send the word 'unused' in the Username field for all future MQTT Connect requests.
Generating a Signed Bootstrap Certificate with OpenSSL:
- Begin by creating a device private key. This key should be distinct from the Registry's CA certificate and private key. Use the following command to generate a 2048-bit RSA private key:
openssl genpkey -algorithm RSA -out rsa_private.pem -pkeyopt rsa_keygen_bits:2048
- Next, create a CSR from the device private key using a SHA-256 signature with the following command:
openssl req -new -sha256 -key rsa_private.pem -out rsa_cert.csr -subj "/CN=unused-device"
This is the same private key you will use to sign the JWT.
- Create a public key and get it signed it with the Registry CA's private key. The following command generates a signed RS256 certificate that meets the public key certificate requirements:
openssl x509 -req -in rsa_cert.csr -CA ca_cert.pem -CAkey ca_private.pem \
-CAcreateserial -sha256 -out rsa_cert.pem
This signed certificate can then be used as the Bootstrap certificate.
Zero Touch Provisioning Connection details
The table below displays the information required by the device to present to OmniCore. It is important to note that the MQTT CONNECT username field must carry the Bootstrap certificate. OmniCore verifies that the Bootstrap certificate is signed by a CA registered with the registry. To demonstrate ownership of the Bootstrap certificate, a JWT must be signed using the private key associated with the Bootstrap certificate. Upon successful authentication with OmniCore, the Bootstrap certificate will be registered for the device
| Mqtt Connection Field Key | Mqtt Connection Field Value |
|---|---|
| Client ID | subscriptions/{subscription-id}/registries/{registry-id}/devices/{device-id} |
| Host | hostprefix.mqtt.korewireless.com |
| Port | 8883 |
| Username | Bootstrap certificate |
| Password | JWT Token |
| SSL/TLS | True |
| Certificate | Available |
| SSL Secure | On |
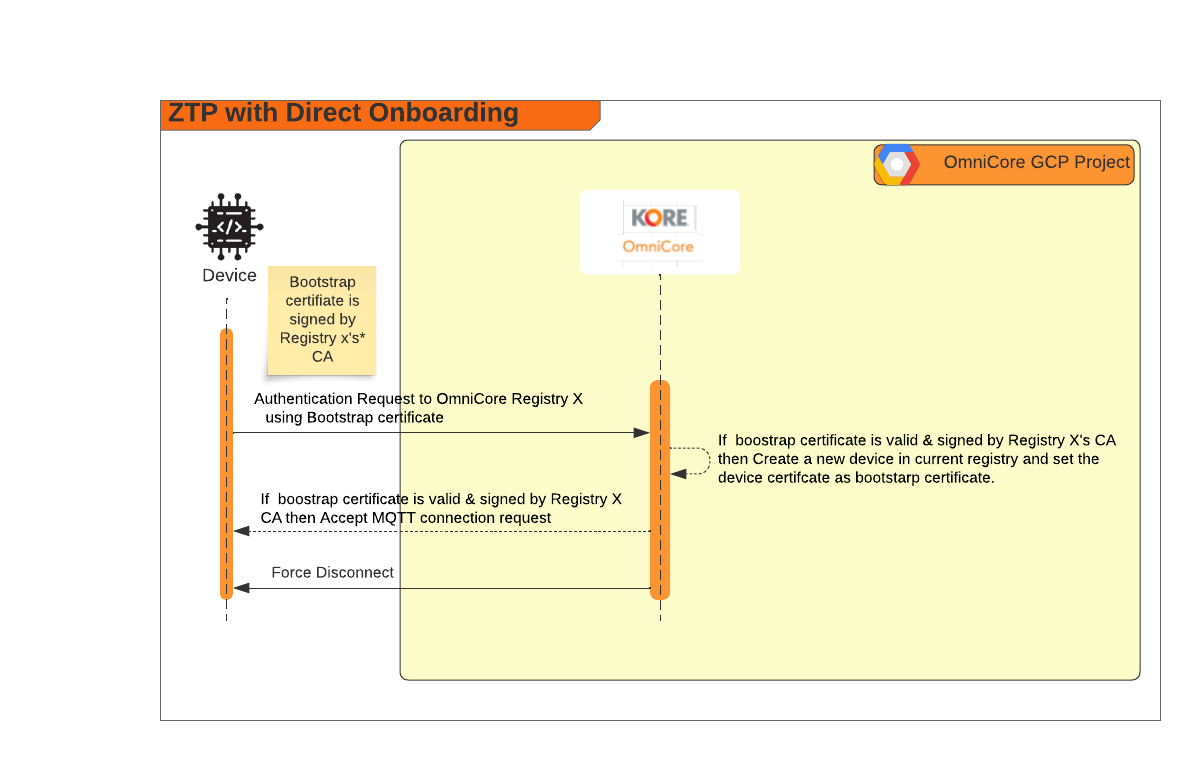
Zero Touch Provisioning With Direct Onboarding
Direct Onboarding is a simple and straightforward method of Zero Touch Provisioning, compared to Custom Onboarding. With Direct Onboarding, devices are immediately onboarded once OmniCore confirms three things:
- The bootstrap certificate is signed by a registry CA.
- The JWT certificate verifies that the device possesses the private key associated with the bootstrap certificate.
- The device ID does not already exist in the system
Diagram of the flow
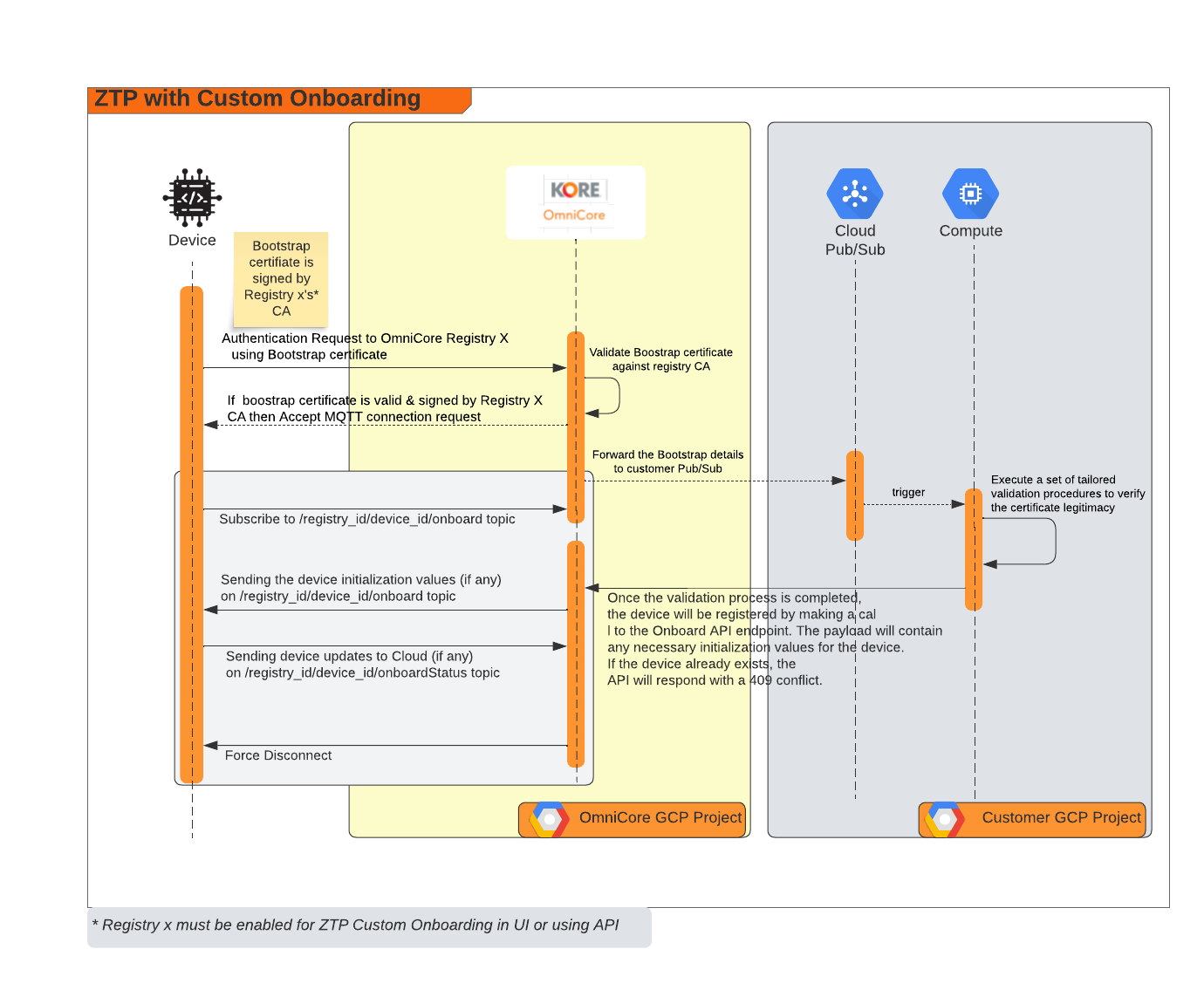
Zero Touch Provisioning With Custom Onboarding
In the case of Zero Touch Provisioning with Custom Onboarding, KORE OmniCore will forward the provisioning request to the customer's pub/sub system. The customer can inspect the incoming request and run additional validations to determine whether to onboard the device or not. If the decision is to onboard the device, the customer's program can call the OmniCore API to add a new device. If initialization values are required by the device, the customer's program can send the necessary payload in the earlier API request, which OmniCore will forward to the device's command topic.
However, if the device already exists, OmniCore will return a 409 conflict error.
Diagram of the flow
Codelab Guide
ZTP is only available for MQTT Devices.